2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
With $4.1 billion lost to DeFi hacks in 2024, the question of security in cryptocurrency exchanges has never been more pressing. The advent of blockchain technology has transformed how we conduct transactions, yet it has also opened the door to various cybersecurity threats that can jeopardize digital assets. In this article, we aim to outline the best practices for cryptocurrency exchange security in 2025, ensuring that both exchange operators and users can navigate the digital landscape safely.
Understanding Cryptocurrency Exchange Security
Cryptocurrency exchanges serve as the backbone of the crypto economy, facilitating the buying, selling, and trading of digital assets. However, they can be vulnerable to attacks and hacks if not properly secured. To emphasize this, consider a physical bank vault that protects your money. Just as organizations invest in vaults to safeguard physical currency, cryptocurrency platforms must adopt stringent security measures to protect digital assets.
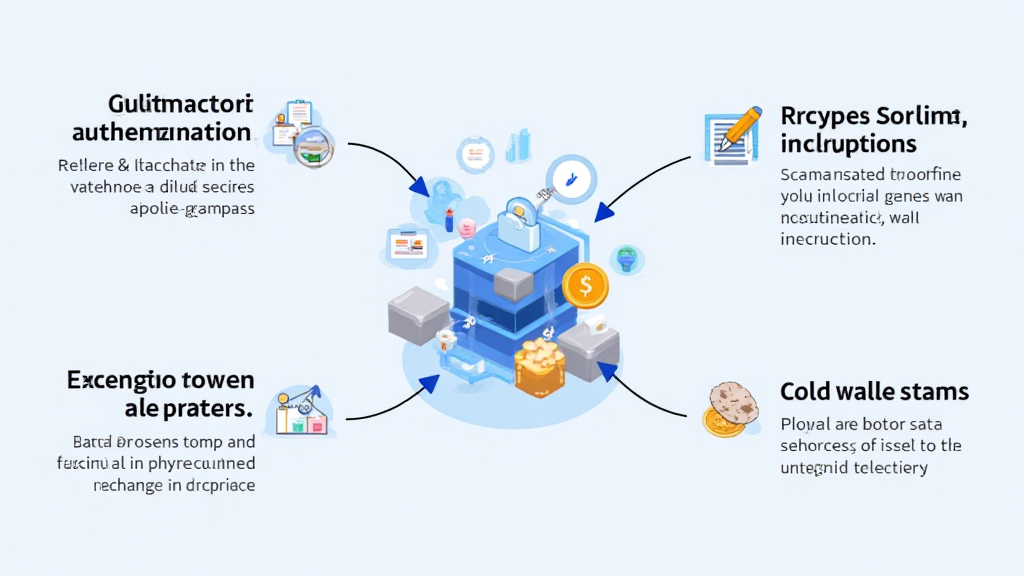
The Importance of Multi-Factor Authentication
One of the most fundamental security practices is implementing a Multi-Factor Authentication (MFA) system. MFA requires users to provide two or more verification factors to gain access, adding an additional layer of defense.
- **Something You Know:** Passwords or PINs are the first layer of defense.
- **Something You Have:** A security token, mobile app, or SMS code acts as a second factor.
- **Something You Are:** Biometric data, such as fingerprints or facial recognition.
By integrating MFA, cryptocurrency exchanges can significantly reduce the risk of unauthorized access.
Best Practices for Wallet Security
Wallet security is an essential aspect of cryptocurrency exchange security. Exchanges often utilize a combination of hot and cold wallets to manage funds.
- **Cold Wallet:** Keep most of the funds in a cold wallet (offline) to protect against online hacks.
- **Hot Wallet:** Maintain a minimal amount in a hot wallet for immediate trades, but ensure it has robust security measures in place.
Using hardware wallets, such as the Ledger Nano X, can dramatically reduce the likelihood of hacks, providing a physical form of secure storage.
Regular Security Audits Are Essential
Conducting regular security audits is vital for identifying vulnerabilities. Engaging third-party security firms to audit smart contracts can uncover potential risks before they can be exploited.
As an analogy, think of regular system audits as routine medical check-ups. Just like we monitor our health to prevent serious conditions, exchanges should regularly monitor their systems to prevent security breaches.
- **Penetration Testing:** Organizations can simulate attacks to discover weak spots.
- **Reviewing Code:** Code audits by professional teams can help catch bugs and vulnerabilities in smart contracts.
According to Chainalysis, over 90% of hacks stem from poorly audited smart contracts.
Data Encryption and User Privacy
Data encryption is a cornerstone of protecting user information and transaction details. Every exchange should utilize strong encryption protocols to safeguard sensitive data.
- **End-to-End Encryption:** This ensures that data remains private while in transit between users and exchanges.
- **Regular Updates:** Always update encryption protocols to use the latest standards.
Establishing trust is crucial. Exchanges need to demonstrate commitment to user privacy, and effective encryption practices can bolster credibility.
Compliance with Regulations and Standards
In the evolving world of cryptocurrency, staying compliant with local and international regulations is paramount. Understanding the evolving landscape of tiêu chuẩn an ninh blockchain can help to reinforce security measures.
- **Know Your Customer (KYC):** Implementing KYC practices not only provides legal assurance but can also deter potential fraudsters.
- **Anti-Money Laundering (AML):** Complying with AML regulations ensures that the exchange only deals with legitimate transactions.
In Vietnam, the regulatory environment is rapidly changing, with users showing an increasing interest in cryptocurrency, necessitating that local exchanges adhere to stringent security and compliance measures.
Enhancing User Education and Awareness
Users are often the weakest link in security. Therefore, educating users about safe practices and potential threats is crucial in the cryptocurrency ecosystem.
- **Phishing Awareness:** Users should be informed about phishing attacks and how to identify suspicious links.
- **Password Management:** Encourage users to use strong, unique passwords and password managers to guard against breaches.
Online resources and guides can provide users with the skills needed to navigate the crypto world safely.
Conclusion: The Future of Cryptocurrency Exchange Security
As we look toward the future of cryptocurrency exchange security in 2025, embracing these best practices will be critical. By implementing multi-factor authentication, securing wallets, performing regular audits, ensuring data encryption, complying with regulations, and educating users, exchanges can establish a secure environment for all participants.
As the user base, especially in regions like Vietnam, continues to grow, cryptocurrency exchanges must prioritize security to build trust and encourage industry adoption. With evolving threats, the adoption of comprehensive security practices will determine success in the cryptocurrency exchange landscape.
For more information on cryptocurrency best practices and security measures, visit hibt.com.
This article was authored by Dr. Mark Henderson, a blockchain security expert with over 15 published papers in the field and the lead auditor for several notable crypto projects. Not financial advice. Consult local regulators.