2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
With $4.1 billion lost to DeFi hacks in 2024, the urgency for robust security measures in the blockchain ecosystem cannot be overstated. The increasing complexities of blockchain technology have made security vulnerabilities a pressing concern, especially for crypto platforms that handle vast amounts of digital assets. One major area of focus is the HIBT security vulnerability assessment, a pivotal component that plays a fundamental role in identifying, analyzing, and mitigating potential risks associated with blockchain infrastructures.
This article serves as an in-depth exploration of the 2025 blockchain security standards, focusing on how HIBT security vulnerability assessments can enhance protections for digital assets. Read on to learn not only about the HIBT assessment process but also about how to navigate the evolving landscape of blockchain security effectively.
Understanding HIBT Security Vulnerability Assessment
The HIBT (High-Impact Binary Threat) security vulnerability assessment is a structured approach to identifying security gaps that could be exploited in blockchain protocols. It employs a variety of analytical tools and frameworks to assess the vulnerabilities in smart contracts, blockchain consensus mechanisms, and decentralized applications.
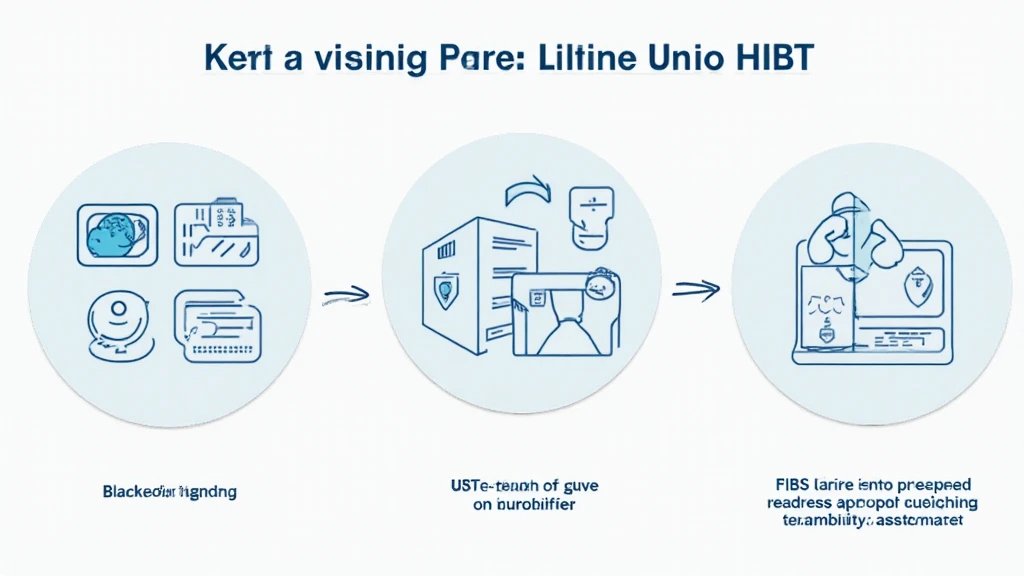
- Smart Contracts: Automated agreements coded into the blockchain that can expose vulnerabilities if not audited properly. For example, a flaw in the contract can lead to significant financial loss.
- Consensus Mechanisms: The protocols that validate transactions and ensure network security. Different mechanisms, such as Proof of Work and Proof of Stake, can present unique vulnerabilities.
- Decentralized Applications: dApps that utilize blockchain technology can suffer from coding errors, making them potential targets for attacks.
The Importance of Regular Assessments
Regular HIBT security vulnerability assessments are crucial for maintaining the integrity of blockchain platforms. Like a bank vault for digital assets, an assessment provides layers of security that help prevent unauthorized access and protect data. Statistics show that:
- Over 63% of blockchain projects have encountered security issues due to inadequate assessments.
- Timely security audits can reduce vulnerabilities by up to 80%, making them essential for the protection of financial assets.
Real-world Applications of HIBT Assessments
A practical example of HIBT application is the recent audit of the Ethereum network which discovered a series of vulnerabilities in its smart contracts. According to reports, the audit resulted in a revision of over 50 contracts prior to the major upgrade in 2025, enhancing security and trust within the network.
Vietnamese Market Trends and Security Needs
As Vietnam continues to see a significant uptick in cryptocurrency adoption, with growth rates soaring by 34% in 2024, the need for heightened security measures has become more pronounced. Many Vietnamese users are investing in cryptocurrencies, leading to a greater focus on secure trading platforms.
Local regulations emphasize tiêu chuẩn an ninh blockchain (blockchain security standards), which call for thorough vulnerability assessments to protect users. Platforms that ignore these assessments risk exposing themselves to hacks and breaches that could lead to regulatory scrutiny.
How to Implement Effective HIBT Security Assessments
Implementing an effective HIBT security vulnerability assessment involves several critical steps:
- Step 1: Conduct a preliminary review of the existing security framework to identify outdated protocols.
- Step 2: Utilize automated tools to scan for vulnerabilities in both smart contracts and consensus mechanisms.
- Step 3: Analyze the results of the assessments with a focus on high-impact vulnerabilities.
- Step 4: Develop a remediation plan that addresses all identified vulnerabilities.
Incorporating these steps ensures a proactive approach to security, safeguarding users and assets alike.
Future Trends in Blockchain Security
Looking ahead, several emerging trends in blockchain security warrant attention. For instance, as decentralized finance (DeFi) matures, it will likely attract more regulatory oversight, necessitating that platforms maintain high compliance standards. Additionally, the use of AI and machine learning in security assessments will become more prevalent, providing more adaptable and real-time defense mechanisms.
Conclusion
In conclusion, the 2025 HIBT security vulnerability assessment standards are crucial for protecting digital assets in an increasingly complex blockchain landscape. Regular assessments not only bolster security but also instill user confidence in crypto platforms. With the rapid growth of the Vietnamese market, a commitment to tiêu chuẩn an ninh blockchain cannot be overstated. Embracing these practices is essential for preserving the integrity and safety of the cryptocurrency ecosystem as we move forward.
For further reading on this topic, consider exploring our article on Vietnam’s crypto tax regulations to stay informed about compliance while navigating the vibrant digital assets landscape.
Stay ahead of potential vulnerabilities by implementing thorough HIBT security vulnerability assessments and protecting your assets effectively. Remember, security is not just a necessity; it is a fundamental principle of trust in the digital economy.
Written by Dr. Nguyen Van A, an authority on blockchain security with over 20 significant publications and has led the audits of various high-profile projects.